If you have an Azure environment when you have your DNS servers in a separate vNet from your new AKS environment you’ll notice that you get an error when deploying the AKS environment which looks something like this.
Agents are unable to resolve Kubernetes API server name. It’s likely custom DNS server is not correctly configured, please see https://aka.ms/aks/private-cluster#hub-and-spoke-with-custom-dns for more information.
The fix for this is actually pretty straightforward, but I’m going to give you a little background on why this happens.

The reason that this happens is that as part of the deployment process for an AKS platform, a private DNS zone is created. This Private DNS zone allows the cluster to find the IP address of the AKS cluster’s management services. The name of this DNS domain is {guid}.privatelink.{azureRegion}.azmk8s.io. Something like this (with the GUID obfuscated).
If you look at the DNS zone, you’ll see that it contains a record of the private IP address of the AKS cluster.
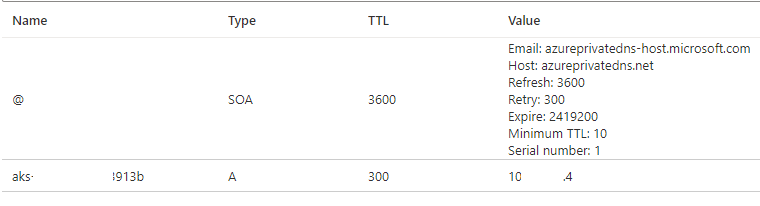
When the Private DNS zone is created, the Azure deployment script creates a network link for this Private DNS Zone for the Azure vNet which the AWS environment is in. If your internal DNS Servers (which are the DNS Server IP Addresses for the vNet) are in that same vNet that the AKS environment is in, then everything will just work. However, when the DNS servers are in a different vNet from the AKS environment this won’t work as the DNS server vNet isn’t mapped to the Private DNS zone.
In order to fix this you’ll need to make changes to the Private DNS zone as soon as the zone is created, but before the AKS environment is up and running. Doing this is pretty straightforward to do.
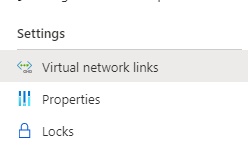
The first step is going to tell the Azure portal (or CLI, or PowerShell) to create the AKS environment. Once the deployment has started creating, in the Azure Portal bring up the Private DNS zones list. When I have been deploying AKS environments, the Private DNS zone usually shows up after 2-3 minutes, but there’s no guarantee for the timing. Use the refresh button on the page and wait for a new Private DNS zone to appear. Once it shows up, navigate to “Virtual network links” on the menu on the left. You can find “Virtual network links” under the Settings group.
When you open the “Virtual network links” you’ll see a page that looks like this with a link to the vNet which holds the AKS environment.
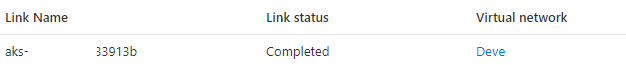
When the page is opened simply click the add button, and create a network link to the vNet which contains the DNS servers as I’ve done in the screenshot below. Adding a network link requires simply putting in the name of the link and selecting the subscription and virtual network from the drop-down list.
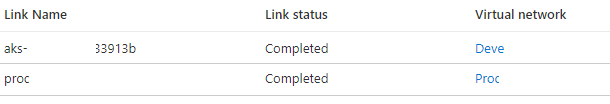
Once the change is made and the new link is deployed the AKS environment will finish deploying and start as normal.
Denny

One Response