Microsoft Azure has a great feature within it called Private Endpoints. With Private Endpoints, you can connect to the Platform as a Service. The Private Endpoint is configured to use a private IP Address instead of routing your connection over the public Internet. This then lets you disable the public endpoint, closing the service off from the public Internet completely. There’s a little work that sometimes needs to be done with Private DNS zones to make everything function correctly, and everything will work great using Microsoft Edge, Google Chrome, Apple’s Safari, or just about any other web browser except Firefox when you are using the DNS over HTTPS (DoH) feature. Let’s look at the why and how to fix it (which is depressingly easy).
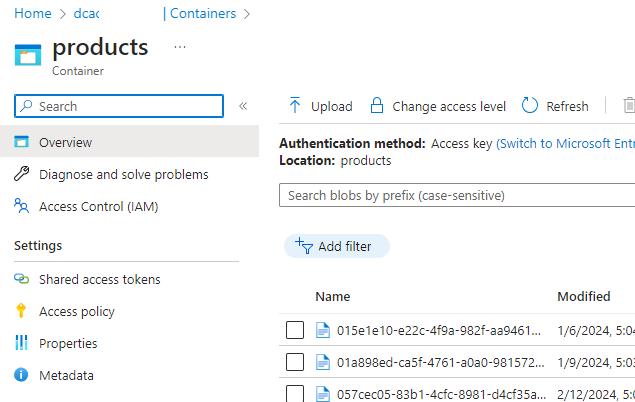
As you can see from the screenshot of one of DCAC’s Azure Storage Accounts, which has a private endpoint, everything works as expected in Microsoft Edge.
However, when you use the same Storage Account (or any Azure resource using a Private Endpoint), you’ll get a message saying that you are trying to connect to a public endpoint, as shown in the second image to the right.
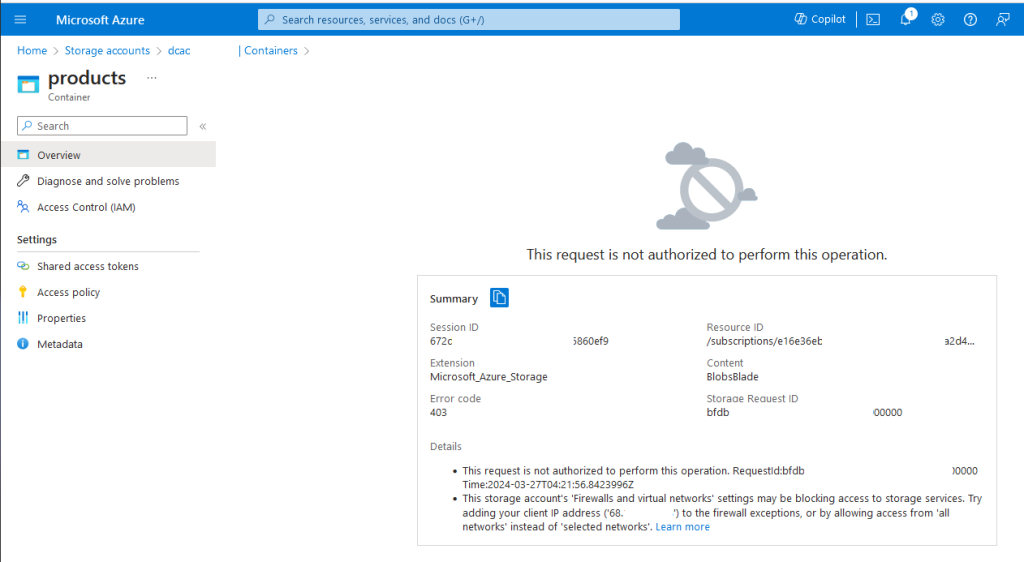
This is because of how private endpoints work and DNS over HTTPS works. So, let’s look at how Private Endpoints work. When you go to connect to a Storage Account, for example, your computer does an NS lookup for that storage account. For example, we’ll use the storage account dcac1 and use blob storage, so the endpoint that we connect to is dcac1.blob.core.windows.net. Our computer does a DNS lookup for dcac1.blob.core.windows.net, and it returns whatever IP address Azure is using to host that storage account, we’ll say 205.25.52.142. When we have a Private Endpoint in place, that Private Endpoint gets a private IP address from the Azure Subnet that you create the Private Endpoint in, we’ll say 10.0.0.5.
This only works when the DNS server that you are using (typically your Windows Active Directory domain controller) sends the requests for Azure resources to a DNS server that you are hosting within Azure (again, typically another Active Directory Domain Controller), which then forwards the request to the Microsoft Azure DNS Service. When this happens, the Azure DNS Server sees that there’s a private DNS zone setup for the blob.core.windows.net namespace, and instead of returning the 205.25.52.142 address, it returns the 10.0.0.5 address, allowing you to connect to the Private Endpoint without ever knowing that there’s been a change.
So the question then becomes, how does Firefox and their DNS over HTTPS service break this? It’s all in the name resolution. Because Firefox is using the DOH feature (I hope whoever named that loves the Simpsons TV Show), it does the DNS resolution by sending the DNS requests off to a Mozilla service to resolve the name to IP, which means that the browser doesn’t know about the private endpoint because the DOH DNS servers don’t have any way to determine that storage account back to the private DNS address.
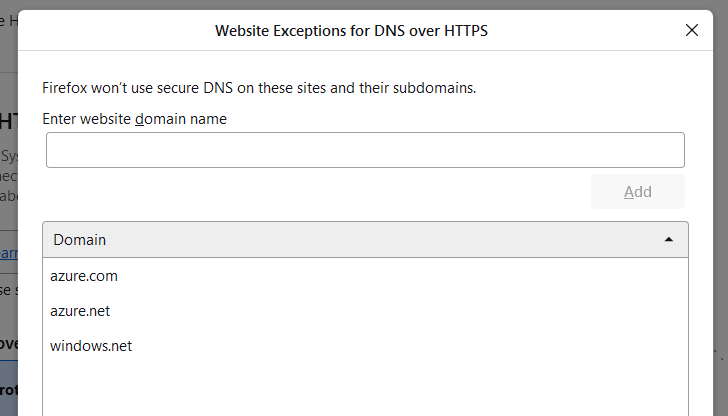
The next question becomes, how do we fix this? Thankfully, that is pretty easy. In your Firefox browser, click the menu at the top right and click settings in the menu that opens. Click on the Privacy & Security section, scroll down to the DNS over HTTPS section, and click the Manage Exceptions button. In the window that opens, add exceptions for azure.com, azure.net, windows.net, and any other suffixes that are being used for Private Endpoints. Once those are entered, click Save Changes (blue button at the bottom), and you should be able to access the Private Endpoint successfully via Firefox.
Denny

