
One of the great things about Office 365 / Azure Active Directory accounts is that the end-users can reset their password and that password change will change their on-premises Active Directory password as well as their Azure Active Directory password. This all works wonderfully until you put the server which is running AD Connect (the software that syncs your Active Directory to Azure Active Directory) behind the Azure firewall, and you start blocking traffic from the AD Connect server.
In my configuration, I had access on ports 80 and 443 to the AzureActiveDirectory service tag, like everything online says is needed. But users were still getting an error when doing password resets in the Office 365 portal. The weird thing was, that I couldn’t see anything getting blocked by the Azure Firewall.
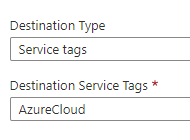
I created an outbound rule for the specific IP Address and allowed ports 80 and 443 with a target service tag of “AzureCloud”. This grants this machine access to the known Microsoft Azure front end IP address ranges; which appears to allow the Self Service Password Change features to begin working.
Denny
